The ITAM Roundup: 1/28/24
Nvidia CEO Jensen Huang meets with TSMC in Taiwan, discusses AI chip shortage concerns over dinner
Nvidia CEO Jensen Huang met with executives from TSMC in Taiwan to discuss concerns about the shortage of AI hardware chips. He mentioned that Nvidia is "very severely supply-constrained" in the AI hardware sector, emphasizing the efforts of TSMC and supply chain partners to meet the growing demand for AI-related products, particularly GPUs equipped with Tensor cores. Huang's visit to Taiwan and his proactive approach to addressing supply constraints underscore Nvidia's commitment to the market, following a similar visit to mainland China, where the company has been preparing China-specific GPU chips since November 2023.

Google, NVIDIA, Microsoft, and Others Collaborate With U.S. Government for AI Research
Leading tech firms are teaming up with the U.S. government and the National Science Foundation for the National Artificial Intelligence Research Resource (NAIRR) pilot program. This initiative, stemming from President Biden's executive order, aims to provide U.S. educators and researchers with advanced AI resources and support. NVIDIA is contributing $30 million, mainly through access to its DGX platform, while Microsoft is providing $20 million in Azure compute credits, and OpenAI is donating $1 million for AI safety and societal impact research. The program will have a two-year proof-of-concept phase before becoming a comprehensive resource for various AI research aspects.

Salesforce Laying Off 700 Workers in Latest Tech-Industry Downsizing
The trend continues, this time with Salesforce laying off approximately 700 employees (~1% of its workforce), following a 10% reduction in staff the previous year. This move is seen as part of an ongoing effort to cut costs and focus on growth. Salesforce has 1,000 open positions remaining within the company, suggesting that these layoffs may be more about workforce adjustment than a significant change in strategy, driven by pressure from activist investors to improve profit margins.
The State of IT Spend in 2024: Computing Infra and Tech Staffing
This 2024 report analyzed how organizations allocate their budgets across eight major IT spending categories, including hardware, software, cloud-based services, managed services, facilities and power, telecommunications, IT labor, and internal services. The study revealed that most organizations prefer a balanced approach, with less than 5% opting for either a fully in-house or outsourced IT strategy. While cloud-based IT strategies are on the rise, the data highlights the continued significance of in-house capabilities. This analysis aims to offer insights into how organizations make strategic decisions about their IT expenditure.

CIO Talk: Copilots — Dive Right In … Or Wait?
Copilots offer the promise of boosting productivity through AI-powered assistance but come with costs and risks. The author advises prudent executives to carefully analyze the costs, train employees in AI usage, prepare organizational data for protection, and involve risk management teams in Copilot deployment to maximize benefits while minimizing risks.

What are the Best Practices for SaaS Security?
Key challenges in SaaS security include limited visibility into SaaS applications, the need for privileged access management, and the risk of insider threats. Implementing some best practices, such as gaining visibility into the SaaS landscape, validating SaaS providers' security certifications and policies, streamlining user lifecycle management, and ensuring data security and compliance, can help organizations protect their data and reputation.

Use Azure Automation and PowerShell to Create a Daily Microsoft Entra Risk Report
You can use Azure Automation and PowerShell to create a daily Microsoft Entra Risk Report. Microsoft Entra ID Protection features can automatically block sign-ins or force password resets based on risk status, but not all organizations have premium subscriptions. To bridge this gap, you can automate the reporting of risk detections using Azure Automation. By scheduling this script, you can receive daily reports of risk events, risky users, and risky service principals, helping you stay proactive in managing security risks.

Got Salesforce?
The below 3 articles from Redress Complianceall help elucidate several different types of salesforce licenses, and how to manage them:
Marketing Cloud
A Salesforce Marketing Cloud license grants access to Salesforce's digital marketing platform, providing tools for email, social media, mobile advertising, and personalized marketing campaigns. It also integrates AI for customer insights and engagement strategies.
User Licenses
Salesforce User Licenses are permissions granting access to Salesforce's CRM platform, defining user roles and capabilities. These licenses come in various types, including standard Salesforce License, Salesforce Platform License, and Identity License, allowing organizations to customize access according to their specific needs.
Feature Licenses:
Salesforce Feature licenses are supplementary permissions that provide access to specific enhanced functionalities within Salesforce, such as Marketing User or Flow User. These licenses are essential for tailoring user capabilities and optimizing Salesforce to meet specific business requirements and processes.
Understanding Cloud Security Posture Management (CSPM)
Cloud Security Posture Management (CSPM) is a set of IT security tools and practices designed to secure cloud infrastructure by identifying misconfigurations and ensuring compliance with security standards. It continuously monitors cloud assets, conducts configuration assessments, and provides automated remediation of security issues. CSPM enhances proactive prevention, strengthens compliance with regulatory frameworks, enables real-time monitoring and rapid incident response, and integrates seamlessly into broader cloud security strategies, complementing other security measures like identity and access management and threat intelligence.

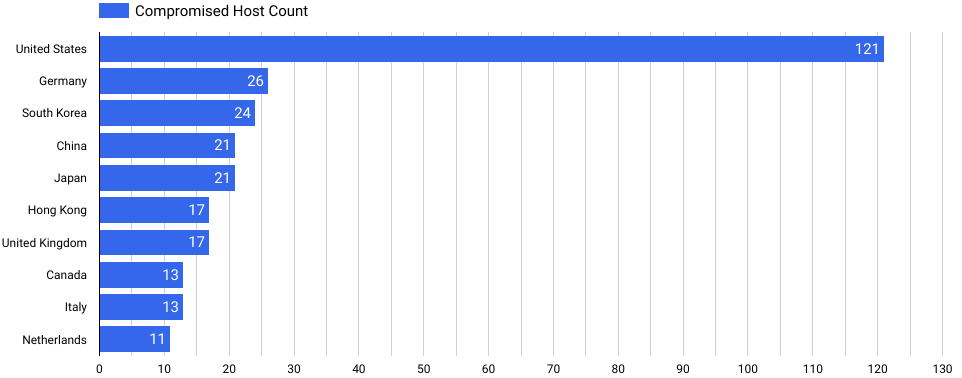
Mass exploitation of Ivanti VPNs is infecting networks around the globe
The Ivanti VPN vulnerability from several weeks ago is becoming a quite popular attack target. Despite a cybersecurity directive for civilian governmental agencies to address the issue, Ivanti has not yet released patches for the vulnerabilities, urging affected users to follow mitigation and recovery guidance provided by the company.